Joomla 4 Security: HTTP Headers plugin
Learning how to secure Joomla 4 is easier than ever before. With the pre-installed HTTP Headers Joomla plugin, you can add up to ten security HTTP headers to protect your data against next-generation cyber attacks.
How to Secure Joomla 4 with HTTP Headers
- Log into your Joomla 4 administrator dashboard (e.g. https://example.com/administrator).
- Select System from the sidebar.
- Under Manage, select Plugins.
- Search for “System – HTTP Headers” and select it.
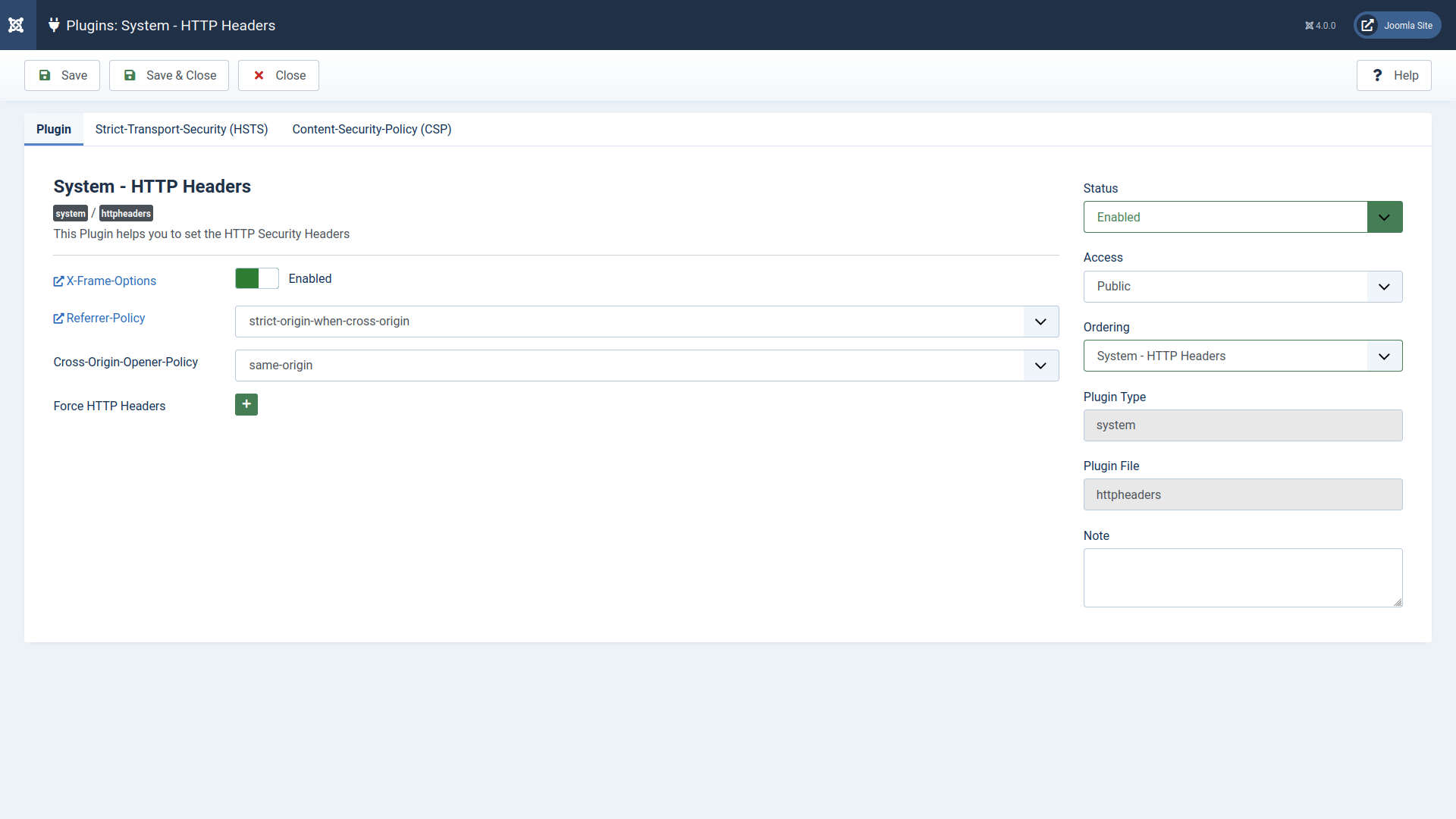
X-Frame-Options specifies whether or how your website can be embedded in another web app or site using iframes. This will harden Joomla against clickjacking. The options for this header are “DENY” and “SAMEORIGIN” (meaning you can embed your website within itself). This is enabled and set to “SAMEORIGIN” by default.
Referrer-Policy can remove sensitive content from the refererr header within URI requests (e.g. password reset URLs). There are nine options in the drop-down menu:
- empty string – no preference
- no-referrer – no referrer info sent
- no-referrer-when-downgrade – full URL unless visiting HTTP page from HTTPS page (default behavior when no policy specified)
- same-origin – only origin (root domain – e.g. example.com instead of example.com/blog) for within the same site
- origin – only origin
- strict-origin – origin only when security level is the same (e.g. HTTPS to HTTPS)
- origin-when-cross-origin – full URL for within the same site, but only origin externally
- strict-origin-when-cross-origin – full URL within site, only origin when protocol security level is the same (e.g. HTTPS to HTTPS), and no info from HTTPS to HTTP
- unsafe-url – full URL (not recommended)
This is set to “strict-origin-when-cross-origin” by default.
Cross-Origin-Opener-Policy (COOP) opens external documents in a separate browsing context group to prevent cross-scripting (XS) attacks.
- unsafe-none – no protection unless opener has stronger COOP policy
- same-origin-allow-popups – page keeps references to same-origin popups
- same-origin – cross-origin documents are opened in a separate browsing context
This is set to “same-origin” by default.
The Force HTTP Headers section allows you to add custom HTTP headers. Most notable among the group is Feature-Policy which blocks unnecessary browser features for user privacy (e.g. camera and WebUSB API). This is now superseded by Permissions-Policy. For example, this disables the user’s mic and webcam while allowing full screen for within the site and a Jitsi Meet video conference:
microphone=(),camera=(),fullscreen=(self “https://meet/jit/si”)
This is set to “interest-cohort=()” by default.
Configure HTTP Strict Transport Security (HSTS) from a tab at the top. HSTS forces web browsers to only load your website using secure (HTTPS) connection. Enabling Joomla HSTS works with SSL 301 redirects to protect against HTTP downgrade attacks.
Notice: You must have a valid SSL certificate on your website while HSTS is enabled. Otherwise, your website will become inaccessible.
Configure Content Security Policy (CSP) from the third tab at the top. CSP prevents web browsers from loading anything in the site that’s not specified in the header (e.g. external sources such as BootstrapCDN and YouTube videos). Configure Joomla CSP in more detail under the Force HTTP Headers section.
Once done with deciding how to secure Joomla, select Save at the top. You can test your security HTTP headers with online tools such as https://securityheaders.com.
Source: inmotionhosting.com
What is wrong?
That imported page keeps on saying this, but nothing further is happening...
1. The "radio buttons" extra field doesn't transfer the values in the additional field, e.g., "yes" or "no," and only enters certain values into the #__fields_values database.
2. The "textarea" extra field with the "Use editor" option checked converts to "textarea" when it should be "editor."
3. In K2, the extra field group is assigned in the category. In Joomla Articles, the category is assigned in the extra field. It would be nice if this were automatically completed. A checkbox could be added if someone doesn't want this option.